High-tech network architecture provides protection against pervasive cyber threats
The United States is the number one target for cyberattacks globally. We do our banking on computers, run our businesses on computers, keep our government records on computers; and on average, one of those computers is attacked by a hacker roughly every 40 seconds. With our daily lives under a near-constant cyber barrage, improving cybersecurity has become a nationwide priority.
Steven Gomez and Richard Skowyra of Lincoln Laboratory's Cyber Security and Information Sciences Division lead development of a technology that could significantly improve cybersecurity within an enterprise computer network, the type of internal network typical of most companies or universities. The project is called Dynamic Flow Isolation, or DFI, and it works to minimize the number of connections within a computer network. To understand why that's so important, start by looking at how most cyberattacks are conducted.
"Attackers break into the network and establish a foothold often on a machine of little interest that's easily compromised, for example via spear phishing [an email scam], and infecting a user's desktop workstation," Skowyra said. "From there, they can spread deeper into the network by using this connectivity with a combination of software exploits and credential theft. Eventually they can access the real target, such as a database containing PII [personally identifiable information]." This strategy is called lateral movement, and almost all the major commercial cybersecurity breaches in the last few years have used it.
The root of this problem is unnecessary connectivity in enterprise computer networks, where machines are typically able to connect with many or all other hosts within the network, all the time. Someone working in the accounting department might never need to access the shared servers used by the company's software developers, but their computer would still be able to send and receive traffic to and from those servers. If any malware infects the first computer, it can use these connections to spread easily to the other hosts in the network; from the accountant, to the shared server, to the computers of every software developer using the shared server. All or a large portion of the computer network is infected can often infected in hours or even minutes.
DFI is easiest to think of in two parts: a policy manager and an enforcement arm. The first system, the policy manager, links security policies to detectable events and defines how network access should change in response to these events. "A simple role-based access control policy could be something like, 'When Bob is logged in, he can access the Github and Exchange servers. When he is logged off, he can only access the ActiveDirectory server.'" Gomez explained. "This policy gets turned into executable code and linked to a sensor that detects log-on and log-off events. When the sensor sees Bob log in, it alerts the role-based access control policy. That policy decides that Bob's computer can now access the Github and Exchange servers….As new sensed events arrive, that comprehensive policy will update. For instance, if Bob logs off, his access to Github or Exchange servers could be revoked if no longer needed." The policy manager uses a set of criteria called policy decision points set by the network administrators to adapt policies when a new situation arises.
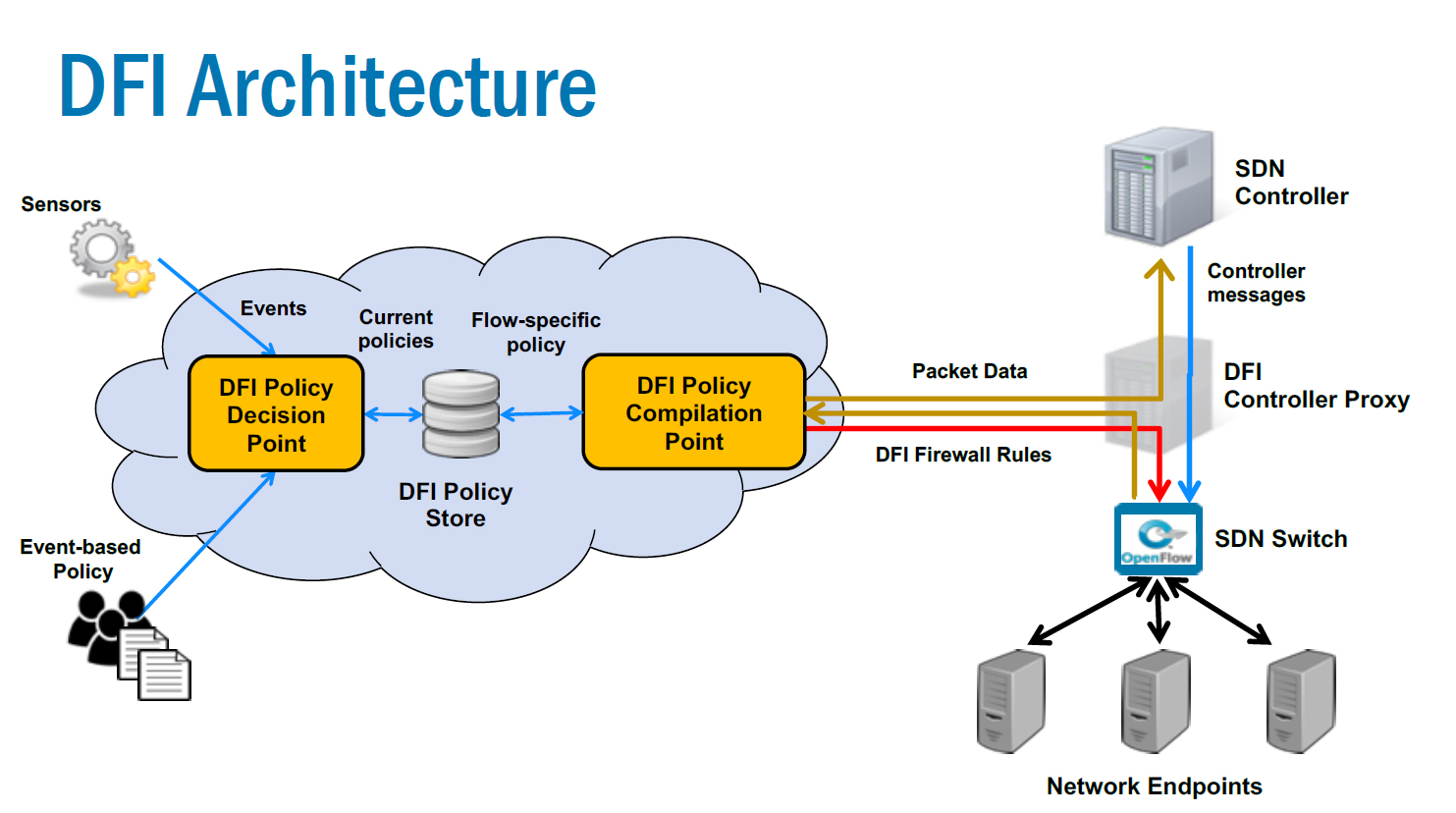
The enforcement arm of DFI examines every new packet that enters the network, and, on the basis of security policies the policy manager has created, determines whether a packet should be allowed to reach its destination or if it should be blocked. DFI maintains a database that links individual identifiers that describe access policies, like usernames, to the low-level information contained in a packet's header, like IP addresses. By employing these linkages, the enforcement mechanism can accurately assess who is being sent what and use the policy manager's security policies to decide whether that packet should reach its destination. The entire system works within an architecture called software-defined networking, or SDN, which is unique in that it centralizes the control plane that the enforcement arm of DFI can refer back to when it needs to decide whether to deliver a packet. This architecture means the policies can be applied case by case, using ones that are up-to-date when the packet is sent.
Ultimately, Dynamic Flow Isolation helps networks to better follow the principle of least privilege, which states that an entity (a computer, a user, etc.) should be able to access the resources that it needs to do its job, and no others. "With DFI, policies can be enforced that change access over time in fine-grained ways," Gomez said. "Ideally, a computer will only be able to access the network resources it needs and only for as long as it needs, based on factors like who is logged into the machine, time of day, current security policies, etc. Critically, packets that should not be allowed are dropped as soon as they enter the network. A vulnerable system will never be infected by an attacker on a machine that should not be able to communicate with the victim normally."
Paula Donovan is the leader of the Cyber Operations and Analysis Technology Group and oversees the Dynamic Flow Isolation project. She emphasized that DFI is well suited to today's national cybersecurity landscape because of the unique way in which it minimizes network connectivity and because of its adaptability. "Our approaches — technology, policies, implementations, etc. — need to be ever-changing because they are protecting against a threat landscape that is ever-changing. Over time, the threats we are addressing continue to grow more sophisticated and efficient," she said.
In 2018, Dynamic Flow Isolation won an R&D 100 Award, which is given annually by R&D Magazine to 100 technologies judged to be the year's most innovative. Still, there are several things that Skowyra and Gomez hope to improve. For instance, when multiple users are on the same device at the same time, disambiguating their traffic within DFI remains a challenge. Other opportunities include scaling up DFI to operate on larger networks, making it more useful for large businesses and government operations. That said, the principles on which DFI operates have proven to be secure in their simplicity. As Donovan put it, "[Dynamic Flow Isolation] minimizes connectivity on networks to only what is necessary for operations; an apartment renter does not need keys to every door in the apartment building."
