Secure Resilient Systems and Technology
Our group develops architectures and technologies for ensuring security and resiliency of mission-critical cyber-physical systems, from drones and satellites to high-performance secure cloud computing. We pursue innovative research and development through the problem analysis, rapid prototyping, and field testing phases, to ultimately deliver our technological solutions for Department of Defense and Intelligence Community uses. Our group is made up of top scientists, engineers, and support staff who share a common passion for solving some of the hardest technical problems relevant to national security.
Featured Projects

cyber security
Secure Radios for Uncrewed Systems
A security module, pre-certified by the National Security Agency, for protecting communications on uncrewed platforms can accelerate the fielding of new systems and open opportunities for the commercial sector.

cyber security
High-Assurance Cryptography
Lincoln Laboratory is developing technologies to meet the highest standards for information security at the tactical edge.

cyber security
Space Systems Cyber-Resiliency
We are researching and prototyping cyber-resilient space systems software that will enable critical national security space assets to withstand, operate through, and recover from cyberattack.

cyber security
Foundational Security for Software
We are creating secure software foundations and applying them to operating systems used widely in mission-critical systems for the Department of War.
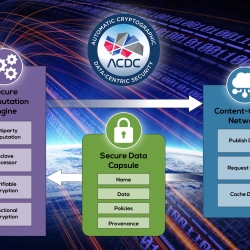
cyber security
Automated Cryptography for Data-Centric Security
We’re shifting the paradigm from system-centric to data-centric security, enabling automatic protection for data throughout all of its uses.
Latest News
Laboratory Story
When the Lab showed me an opportunity to apply my previous research experience in cybersecurity to space systems, I was hooked.
Samuel Mergendahl
Systems Security Architect
Cyber Security and Information Sciences
Secure Resilient Systems and Technology
The prototyping work at the Lab can have a clear aim but multiple paths to get there. I am motivated to find the answers by investigating different directions and trying a variety of creative methods!
Andrea Lin
Secure Systems Engineer
Cyber Security and Information Sciences
Secure Resilient Systems and Technology
I connect deeply with the Laboratory’s mission of technology in support of national security.
Nathan Burow
Computer Scientist
Cyber Security and Information Sciences
Secure Resilient Systems and Technology
Lincoln Laboratory is a perfect fit for me because it has incredible people that love teaching new things; as a recent graduate, this is something I put a lot of value into.
David Langus Rodriguez
Computer Engineer
Cyber Security and Information Sciences
Secure Resilient Systems and Technology
Advancing Our Research
Events
May
27
-
29
Cyber Technology for National Security (CTNS) 2026
MIT Lincoln Laboratory, Lexington, Massachusetts
Our Staff
View the biographies of members of the Secure Resilient Systems and Technology Group.