Foundational Security for Software

"The best defense is a good offense" is a truism in athletics; it is also true for cybersecurity: the best defense is understanding attacks. Consequently, we have investigated the largest classes of vulnerabilities in modern systems and have identified three main legacy design choices that are the root causes of the current insecure software environment. These design choices are 1) the use of unsafe programming languages (such as C/C++), 2) the lack of proper semantics in the processor, and 3) the monolithic, highly privileged design of operating systems (OSs).
To address all three of these problems, we are pursuing a moonshot vision to develop a new computer system design. Our design uses a safe programming language (Rust), semantically rich processors known as “tagged” architectures, and a novel OS design paradigm that leverages fine-grained compartmentalization of OS functions to prevent the largest classes of vulnerabilities.
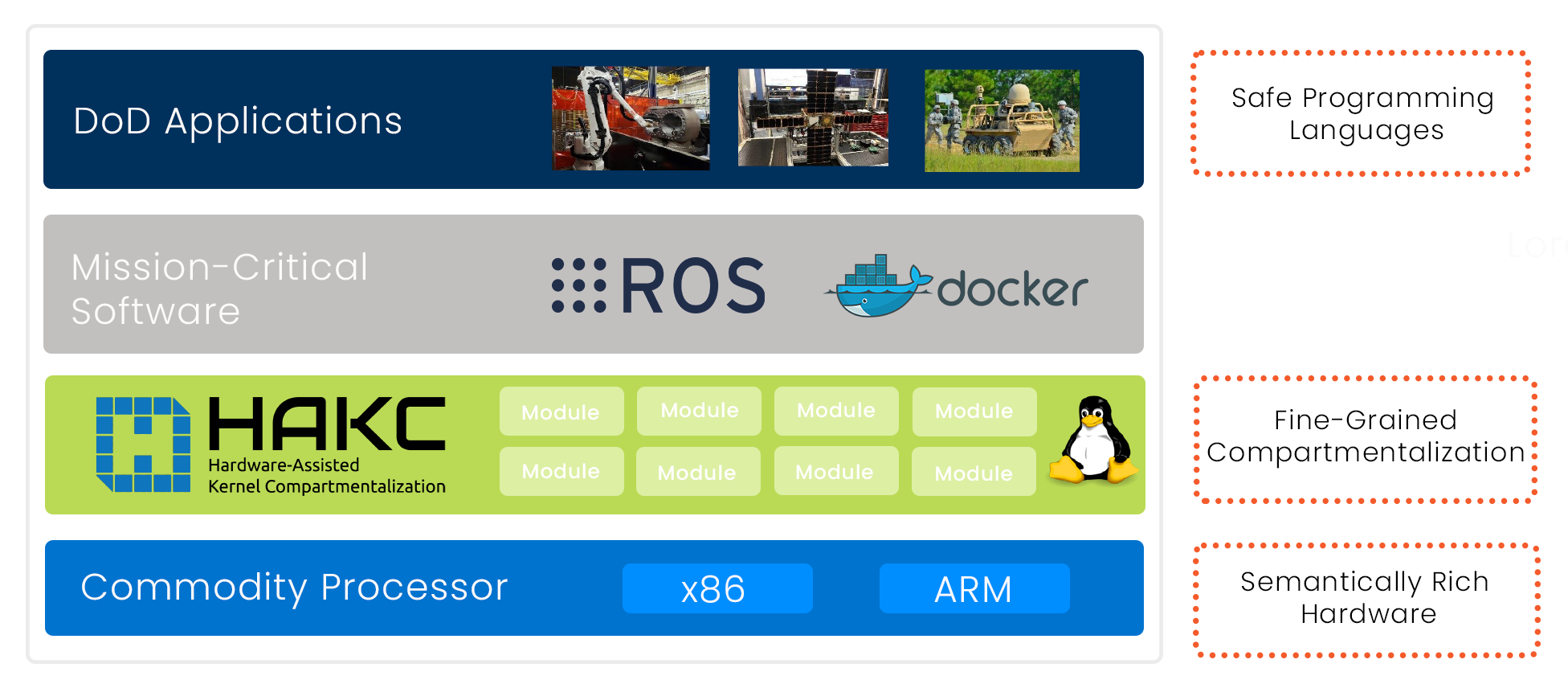
We have further matured these technologies for transition to existing mission systems by applying them to the Linux operating system, which is used widely in enterprise and embedded systems today. Our hardened version of Linux fully supports legacy applications. Leveraging new advancements in security-aware hardware, we compartmentalize Linux into smaller components and modules, each of which has the lowest privilege needed for its functionality. By providing this fine-grained privilege reduction to the Linux OS, we enhance the security of both the OS and the applications and mission functions running on it. Secure-by-design and performant-by-design software platforms provide a secure software foundation for Department of Defense mission systems.





