An adaptable processor optimizes how computing resources are distributed

From smart home systems like Google Home to interconnected sensors for surveillance, many devices now connect wirelessly to the internet and share the useful sensor data they collect (e.g., temperature, presence of intruder) with users. Such Internet of Things (IoT) devices extend beyond consumer use to industry and defense uses. For example, IoT sensors can be deployed for identification and classification tasks like monitoring and securing borders, spotting unauthorized individuals entering restricted areas, and analyzing patterns of life to understand people’s habits or behaviors over time. To apply IoT to these tasks, pertinent data must be detected, processed, and secured. However, low-level processing performed on end users’ platforms is often insufficient to complete such tasks, and outsourcing computationally intensive operations to the cloud presents security risks.
“A low-level computation would be adequate to detect the presence of a voice, for instance, but a high-level computation would be needed to identify that this voice is coming from a particular person,” explains Karen Gettings, technical staff in Lincoln Laboratory’s Embedded and Open Systems Group. “The challenge is enabling hierarchical processing, in which a processor saves power by operating at lower levels of performance until higher levels are required.”
Gettings is part of a team from MIT Lincoln Laboratory and Arizona State University who developed a low-power, self-reconfigurable processor with built-in security and trust to identify and classify subjects of interest, such as voices and objects. Called Reconfigurable Edge Computing for Optimum Resource Distribution (RECORD), the processor is optimized to self-adapt its resources depending on the computations necessary to process sensor data. (Data can also come from generic sources, such as a social media fetch, in which case, the trigger may be a keyword or change in patterns.) Data are processed within a local network close to where they are collected, as opposed to at a data center, which can be hundreds of miles away; this type of processing, which saves time and power, is known as edge computing.
RECORD operates at the lowest power setting and switches to higher-power functionality as needed. A microcontroller, preprogrammed prior to a mission by a human operator with a set of instructions about the specific target of interest, serves as the “brain” of RECORD. The microcontroller communicates with accelerators, which are hardware devices optimized to perform specific functions, like detecting energy, converting signals into frequencies, filtering out data from unwanted frequencies, and machine learning. The microcontroller directs the accelerators, each of which requires a different amount of power, to work in a specific way.
“The microcontroller runs the system at low levels of computation until it sees something that can potentially match what it’s looking for. Then, the microcontroller enables more computationally intensive computations to ensure the right target has been identified,” explains Gettings.
For example, consider a system configured to recognize and obey commands from a precharacterized human voice. RECORD allocates minimal system resources until a low-power accelerator (say, an energy detector) registers a voice signal above background noise from sources like people walking around and distant cars driving by. Then, to characterize and determine whether this voice matches the precharacterized one, RECORD activates higher-power accelerators — such as finite impulse resonance (FIR) filters or other digital signal processing filters to remove noise and other unwanted parts of the signal, fast Fourier transform (FFT) algorithms for converting signals in the time domain to the frequency domain, and neural networks and support-vector machines (SVMs) that enable computers to learn from observational data (i.e., machine learning). Keeping the power-intensive accelerators disabled and only running them when necessary can save power.
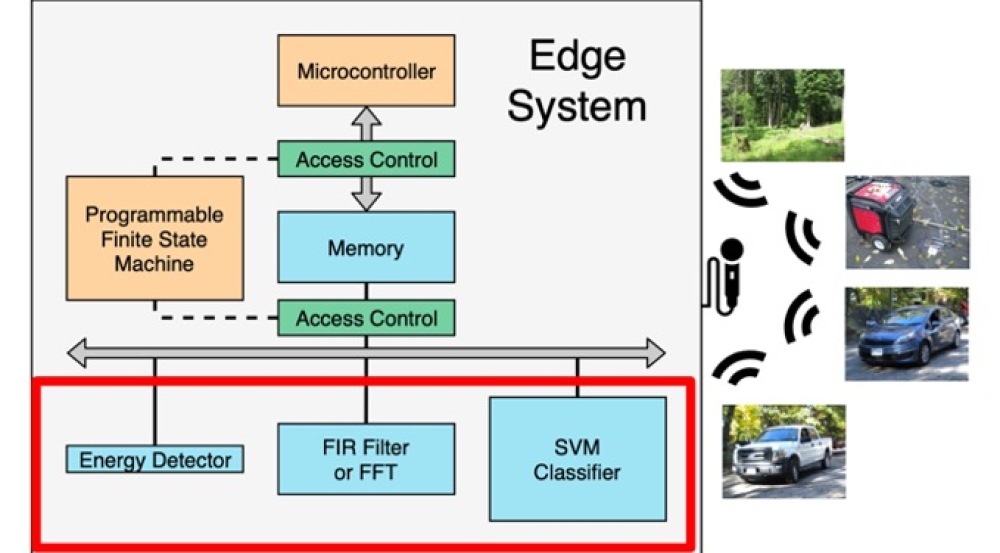
While minimizing compute power, RECORD provides security and data privacy for interconnected sensor systems at all stages, from boot up and operation to data at rest. To secure the processor, Professor Michel Kinsy and his research group at Arizona State provided their expertise in IoT security, applying encryption schemes to protect both the machine learning models used to identify targets and the outputs of these models.
“Many IoT devices, like Amazon’s Alexa and Apple’s Siri, are in a low-power state until they are triggered,” says Gettings. “But, as far as we know, our processor is the only one that continues hierarchical processing even after triggering and secures data after processing.”
The team demonstrated RECORD in a general-purpose integrated circuit called a field-programmable gate array (FPGA), showing the functionality of various accelerators. They also mapped RECORD onto an application-specific integrated circuit (ASIC) – a chip customized for a particular purpose – to assess the processor’s size, weight, and power requirements. An ASIC implementation could boost power savings, but some users will still prefer the FPGA implementation because it provides extra flexibility in terms of reprogrammability while consuming a low amount of power.
Now, the team aims to integrate multiple RECORD processors. Independent devices communicating with each other could improve the precision of identifying and classifying targets, possibly through combining data from a variety of sensors. For instance, one sensor could collect sound data, while another could collect image data. These combined data would increase confidence that the proper target has been identified.
“The accelerator-based processor we developed can improve secure edge computing for various applications, including self-driving cars, speech processing, environmental monitoring, border security, restricted-area protection, and patterns-of-life analysis,” says Gettings.
Inquiries: contact Ariana Tantillo.
Related Links