Automated Cryptography for Data-Centric Security
Today’s security model focuses on securing massive servers and protecting networks. This security approach creates an environment where cyber attackers can focus all of their effort on a small number of large, high-value targets that give massive returns with a single success. This model is responsible for many high-profile incidents, such as the 2015 OPM hack and the 2016 Yahoo! breach, and highlights a flaw in the core design philosophy of the current state of security. Securing users’ data requires restructuring to a distributed, data-centric model.
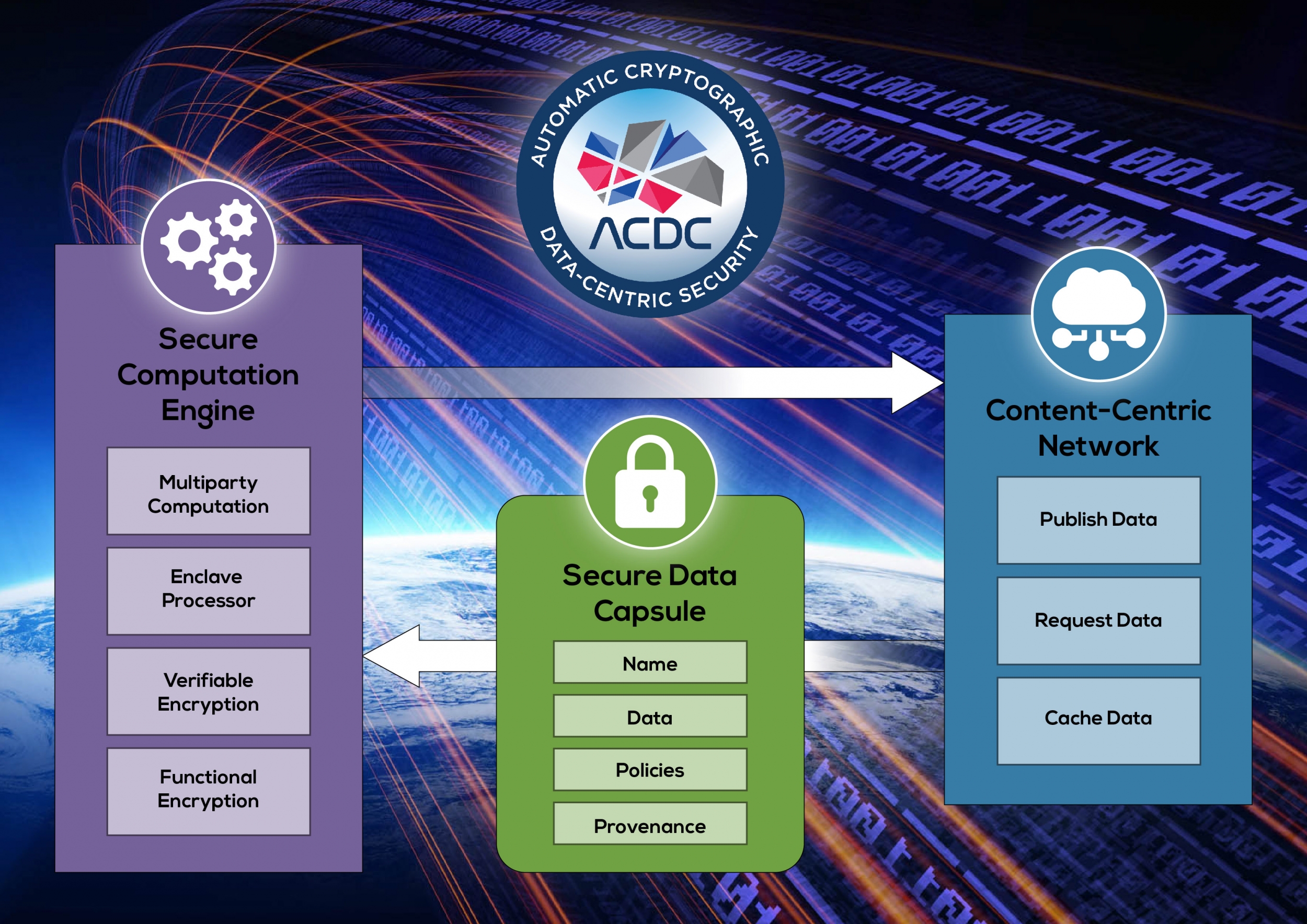
We’re developing just that — a data-centric security architecture that ensures data are used only in authorized and auditable ways. Our goals are to protect the confidentiality, integrity, and availability of data throughout all uses, including not only storage and transmission but also sharing and computation, on devices and networks that may be partially compromised. At its core, our architecture puts all data into encrypted, secure data capsules. Capsules can easily be spread throughout the network and cached redundantly. Access-control policies can be written to ensure the confidentiality and integrity of a capsule, and every data interaction has a permanent record of who acted on the data and what was done. Among their global benefits, these protections can end the era of the “catastrophic” breach, and help ensure the security of critical national assets.
Read more




