Tactical Key Management
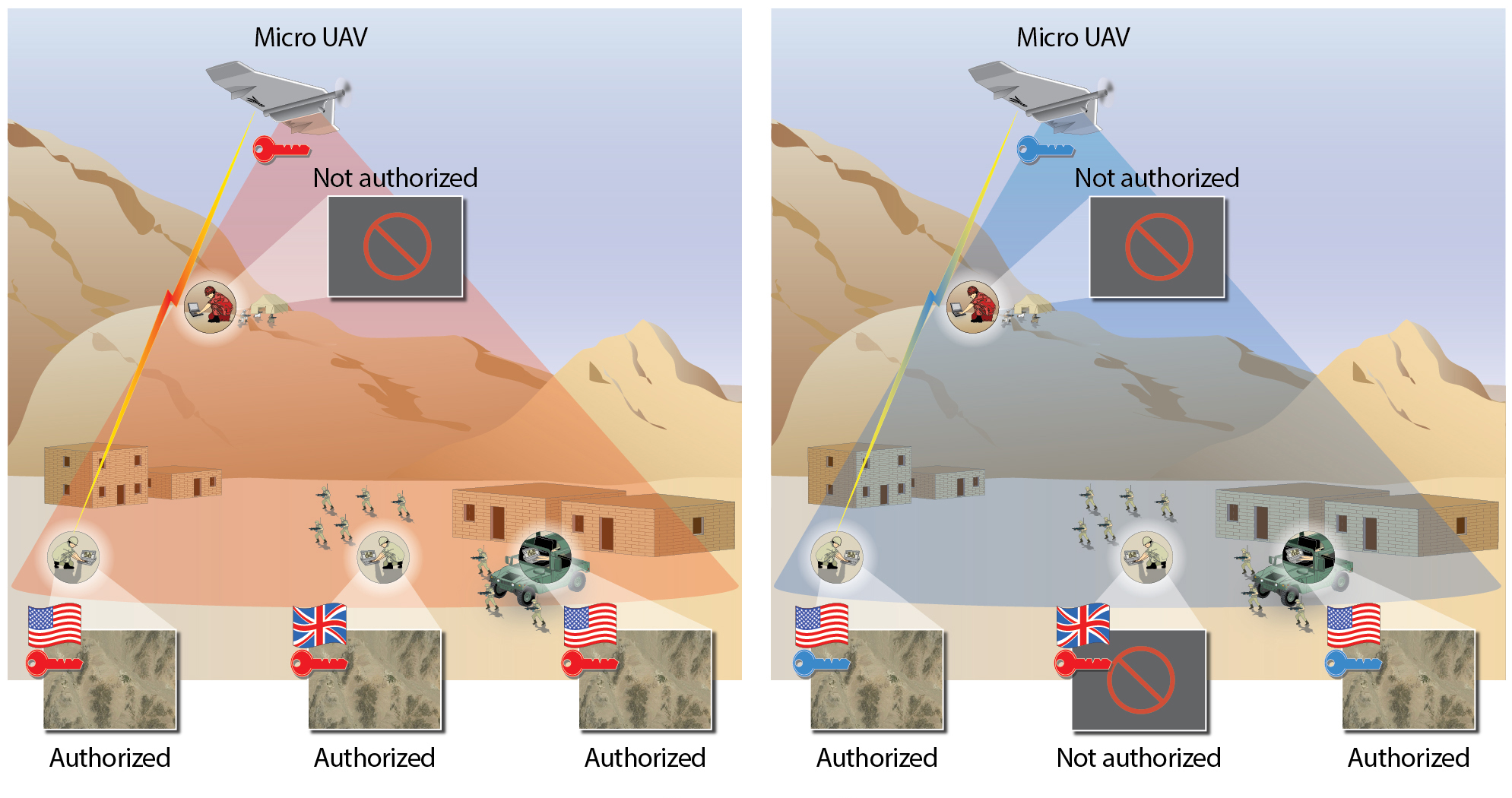
Cryptographic keys are essential to securing digital communications. Because managing these keys — generating, distributing, and revoking them — during a tactical mission consumes an operator’s time and attention, this task is often handled prior to the mission. During a mission, it is difficult to provide real-time key management in response to evolving needs.
To address this difficulty, we developed Tactical Key Management (TKM), a suite of techniques that allows keys to be created, securely distributed, and used dynamically as needed during a mission instead of beforehand. With our approach, devices are put into the field while unkeyed. An operator can generate a mission key at any time directly on the device, without needing to manually load it. Keys are transmitted over the network to the exact set of devices that need them. Likewise, keys can be revoked. This ability makes it possible to respond to dynamic situations, for example, to securely grant a new terminal access to a drone’s video feed or hand off control of a robot to a different user.
There are currently multiple TKM implementations in the field. For our next steps, we aim to further the adoption of TKM technology in unmanned, autonomous, and space-based systems and will improve the compatibility of our system with non-TKM-enabled devices and infrastructures.



