Projects
Tagged As

Secure Radios for Uncrewed Systems
A security module, pre-certified by the National Security Agency, for protecting communications on uncrewed platforms can accelerate the fielding of new systems and open opportunities for the commercial sector.
Tags

High-Assurance Cryptography
Lincoln Laboratory is developing technologies to meet the highest standards for information security at the tactical edge.
Tags

Private Automated Contact Tracing
An automated, Bluetooth-based system helps perform contact tracing in a private, anonymous way, offering a method to reduce disease spread during a pandemic.
Tags

Space Systems Cyber-Resiliency
We are researching and prototyping cyber-resilient space systems software that will enable critical national security space assets to withstand, operate through, and recover from cyberattack.
Tags

Foundational Security for Software
We are creating secure software foundations and applying them to operating systems used widely in mission-critical systems for the Department of War.
Tags
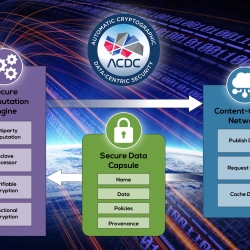
Automated Cryptography for Data-Centric Security
We’re shifting the paradigm from system-centric to data-centric security, enabling automatic protection for data throughout all of its uses.
Tags

Reconnaissance of Influence Operations
New software takes advantage of artificial intelligence techniques to automate the detection and assessment of aggressive influence operations.
Tags

Applied Resilience for Mission Systems
We’re improving and guiding the resilience of Department of War missions by adapting commercial practices and academic research for the development, operation, and sustainment of software-intensive systems.
Tags

Keylime
We're enabling trust in the cloud with this free, open-source key bootstrapping and integrity management software architecture.
Tags

Common Evaluation Platform
Developers can test cybersecurity solutions for government systems by using an integrated circuit modeled on Department of War designs.
Tags