Projects
Tagged As
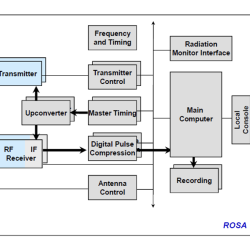
Kwajalein Modernization and Remoting Program Radar Open System Architecture
We developed an open system architecture that reduces the complexity and cost of operations at the Reagan Test Site.
Tags

Reagan Test Site Automation and Decision Support
New software tools provide test operators with automated decision support for directing sensors during increasingly complex tests conducted at the Reagan Test Site.
Tags
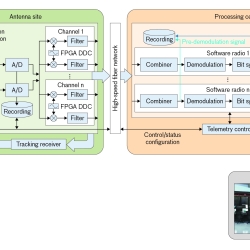
Telemetry Modernization with Open-Architecture Software-Defined Radio Technology
We conducted a software-defined radio technology development program to improve the way telemetered information is collected and processed.
Tags

Reagan Test Site Optics Modernization
Upgrades to the Reagan Test Site’s optical systems combine state-of-the-art focal plane technologies with a wide-area, network-centric, open-system design to allow distributed system command and control while achieving unprecedented metric accuracy.
Tags

High-Assurance Cryptography
Lincoln Laboratory is developing technologies to meet the highest standards for information security at the tactical edge.
Tags
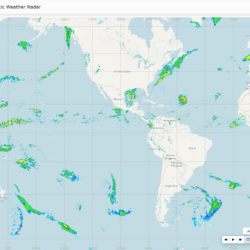
Global Synthetic Weather Radar
By compiling lightning data, satellite imagery, and numerical weather models, the GSWR provides radar-like analyses and forecasts over regions not observed by actual weather radars.
Tags
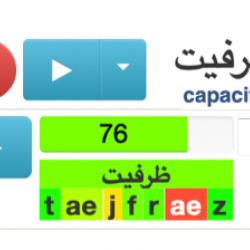
Automatic Pronunciation Feedback
Powered by our automatic speech recognition technology, the Networked Pronunciation Feedback (NetProF) software application helps students practice pronunciation in foreign languages.
Tags

Space Systems Cyber-Resiliency
We are researching and prototyping cyber-resilient space systems software that will enable critical national security space assets to withstand, operate through, and recover from cyberattack.
Tags

Foundational Security for Software
We are creating secure software foundations and applying them to operating systems used widely in mission-critical systems for the Department of War.
Tags

Artificial Intelligence–Guided Ultrasound Intervention Device
Hemorrhage causes 90% of preventable battlefield deaths. AI-GUIDE is designed to address this issue by enabling medics to catheterize a major blood vessel, through which life-saving aid can be delivered, in a pre-hospital setting.
Tags