Projects

Secure Radios for Uncrewed Systems
A security module, pre-certified by the National Security Agency, for protecting communications on uncrewed platforms can accelerate the fielding of new systems and open opportunities for the commercial sector.
Tags

Superconducting Content-Addressable Memories (SuperCAMs)
Unconventional memory circuits can accelerate data processing in cyber sensing devices by reducing the latency of matching complex data patterns to specialized processing pipelines.
Tags

Healthcare-Based Multimodal Recovery Prediction for the Servicemember
This machine learning model will help military and hospital personnel predict when servicemembers and patients may recover following an injury or surgery.
Tags

High-Assurance Cryptography
Lincoln Laboratory is developing technologies to meet the highest standards for information security at the tactical edge.
Tags
Combining Neural Networks and Histogram Layers for Underwater Target Classification
New machine learning methods capture statistical features within sonar data to distinguish between sound sources.
Tags

Private Automated Contact Tracing
An automated, Bluetooth-based system helps perform contact tracing in a private, anonymous way, offering a method to reduce disease spread during a pandemic.
Tags

Materials by Design
A new approach to materials discovery aims to expedite the process of deploying new materials for specific mission needs.
Tags
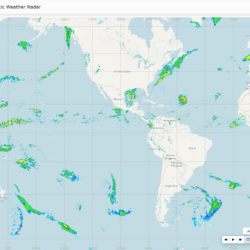
Global Synthetic Weather Radar
By compiling lightning data, satellite imagery, and numerical weather models, the GSWR provides radar-like analyses and forecasts over regions not observed by actual weather radars.
Tags

Space Systems Cyber-Resiliency
We are researching and prototyping cyber-resilient space systems software that will enable critical national security space assets to withstand, operate through, and recover from cyberattack.
Tags

Foundational Security for Software
We are creating secure software foundations and applying them to operating systems used widely in mission-critical systems for the Department of War.
Tags