Projects

Secure Small Satellite Processing Platform
A secure reference architecture enables satellites to recover from cyberattacks and carry on their missions.
Tags

Tactical Key Management
Cryptographic keys can now be created and securely distributed in real time during a mission.
Tags
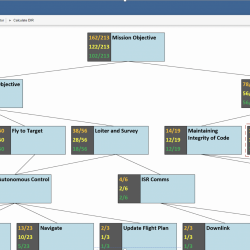
High Assurance Design Environment
A new tool enables mission system designers to design for functionality and security together and provide evidence for how design choices affect a mission’s security posture.
Tags

Seismic-Metamaterial Cloaking to Protect Infrastructure
Novel metamaterials deployed to provide a barrier around critical structures are designed to redirect and attenuate hazardous seismic waves.
Tags
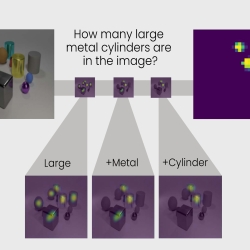
Transparency by Design Network
A new neural network model reveals some of the mystery behind the decision-making capability of artificial intelligence systems.
Tags

Haystack Ultrawideband Satellite Imaging Radar
Lincoln Laboratory created the world's highest-resolution radar for imaging of space objects in support of space situational awareness.
Tags

Advanced ASIC System on Chip for CLASS
A power-efficient application-specific integrated circuit system on chip that performs up to 2 trillion computations per second has potential for use in mobile communication systems.
Tags

Undersea Optical Communications
A system that enables robust, long-distance communications between underwater vehicles exploits laser technology.
Tags

Computer on Watch
An artificial intelligence application that automatically identifies objects in aerial imagery could reduce the time analysts spend in manually combing through images.
Tags

Cyber Adversarial Scenario Modeler and Artificial Intelligence Decision Engine (CASCADE)
CASCADE software simulates cyber attacker and defender actions and recommends multiple courses of action to make systems and networks more secure.
Tags